If you use Microsoft Office you should be on the look out for this new virus that spreads via email.
From McAfee
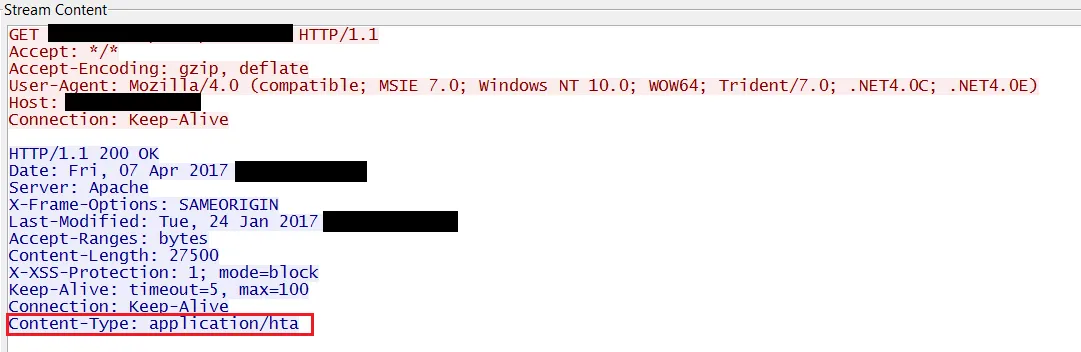
At McAfee, we have put significant efforts in hunting attacks such as advanced persistent threats and “zero days.” Yesterday, we observed suspicious activities from some samples. After quick but in-depth research, this morning we have confirmed these samples are exploiting a vulnerability in Microsoft Windows and Office that is not yet patched. This blog post serves as a heads-up for our customers and all Office users to protect against this zero-day attack. The samples we have detected are organized as Word files (more specially, RTF files with “.doc” extension name). The exploit works on all Microsoft Office versions, including the latest Office 2016 running on Windows 10. The earliest attack we have seen dates to late January. The exploit connects to a remote server (controlled by the attacker), downloads a file that contains HTML application content, and executes it as an .hta file. Because .hta is executable, the attacker gains full code execution on the victim’s machine. Thus, this is a logical bug, and gives the attackers the power to bypass any memory-based mitigations developed by Microsoft. The following is a part of the communications we captured:https://securingtomorrow.mcafee.com/mcafee-labs/critical-office-zero-day-attacks-detected-wild/
Follow @contentjunkie to stay up to date on more great posts like this one.
